Product Introduction⚓︎
Important Notice | JumpServer Vulnerability Notification and Remediation Solution(JS-2023.09.27)
September 2023,Some users have reported discovering Several security vulnerabilities in the JumpServer open-source PAM(Privileged Access Management). They have notified the JumpServer open-source project team about it.
Vulnerability Information:
JumpServer Vulnerability where password reset verification codes can be calculated or inferred,CVE numbering is CVE-2023-42820。
JumpServer Vulnerability where password reset verification codes can be brute-forced,CVE numbering is CVE-2023-43650。
JumpServer Vulnerability allowing authenticated users to perform arbitrary file reads across directories,CVE numbering is CVE-2023-42819。
JumpServer Logic flaw vulnerability allowing authenticated users, after enabling MFA, to use SSH public key authentication, CVE numbering is CVE-2023-42818。
JumpServer Vulnerability allowing users to create access tokens using public keys after enabling global public key authentication,CVE numbering is CVE-2023-43652。
JumpServer Remote Code Execution vulnerability allowing authenticated users to execute arbitrary system commands when connecting to the MongoDB database,CVE numbering is CVE-2023-43651。
The aforementioned vulnerabilities affect the following versions of JumpServer:
JumpServer v2.0.0-v2.28.19
JumpServer v3.0.0-v3.7.0
Secure versions:
JumpServer version = v2.28.20
JumpServer version >= v3.7.1
Remediation solution:
Upgrade JumpServer to Secure versions。
Special Thanks:
We would like to extend our gratitude to the following community users for promptly reporting the aforementioned vulnerabilities to the JumpServer open-source community.
CVE-2023-42820、CVE-2023-42819:@KiruaLawliet & zhiniang peng(@edwardzpeng)with Sangfo
CVE-2023-42818: @pokerstarxy & Ethan Yang(@justlovediaodiao)& Hui Song(@songofhawk)
CVE-2023-43650、CVE-2023-43652、CVE-2023-43651:OskarZeino-Mahmalat(Sonar)
1 What's JumpServer?⚓︎
JumpServer is an open-source Privileged Access Management (PAM) tool that provides DevOps and IT teams withon-demand and secure access to SSH, RDP, K8s, Remote Apps and Database endpoints through a web browser.
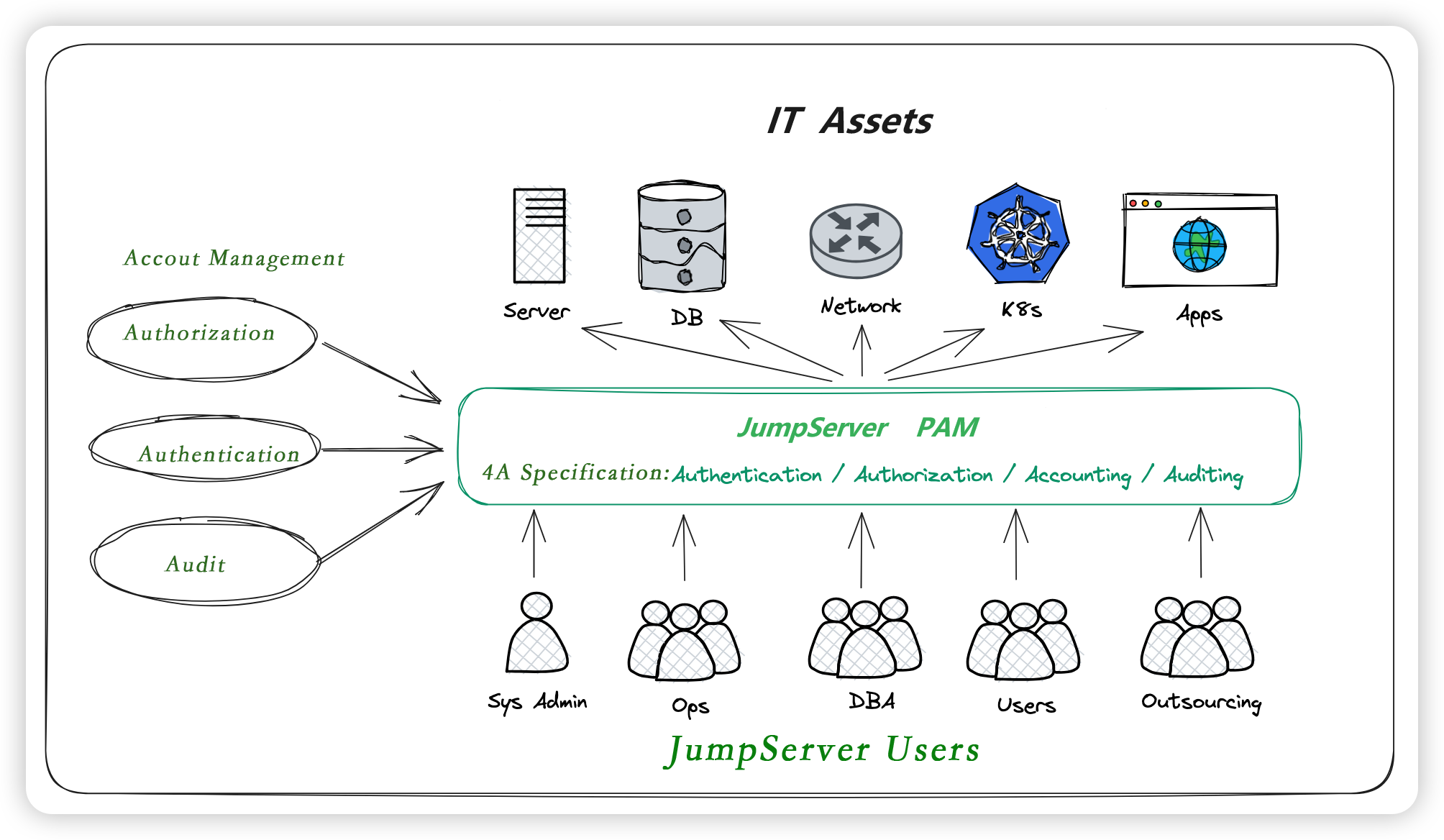
The asset types supported by JumpServer bastion include:
- SSH (Linux / Unix / Network device and so on)
- Windows (Web connetction / Native RDP connection)
- Database (MySQL / MariaDB / Oracle / SQLServer / PostgreSQL / ClickHouse and so on)
- NoSQL (Redis / MongoDB and so on)
- GPT (ChatGPT and so on)
- Cloud service (Kubernetes / VMware vSphere and so on)
- Web station (Web-based management consoles for various systems)
- Applications (Connecting to various applications through RemoteApp service)
Document index
-
JumpServer Introduction
Products introduction Installation and Deployment Demo enviroment Enterprise trial Community forum
-
Feature Guide
User Management Asset Management Account Management Privilege Management
-
Enterprise Application(X-Pack)
Asset access review Connection mode control
Ticket Cloud Synchronization Role list
Account Collection Password modification Account backup
Shot message setting GUI configuration Organization Management Authentication Setting
-
Advanced Learning
2 Product features⚓︎
The distinctive features of JumpServer:
- Open-source:Easy to start,quick online access and installation;
- Distributed:Supports high-scale concurrent access easily;
- Plugin-free:Achieves an optimal Web Terminal experience with just a Web browser;
- Multi-Cloud support:A single system capable of managing assets across various clouds simultaneously;
- Storage on cloud:Video of audit storaged on cloud, and never lost;
- Multi-tenancy:One system, providing services to multiple subsidiaries and different departments simultaneously;
- Various Applications support:Database,Windows Remote application,Kubernetes。
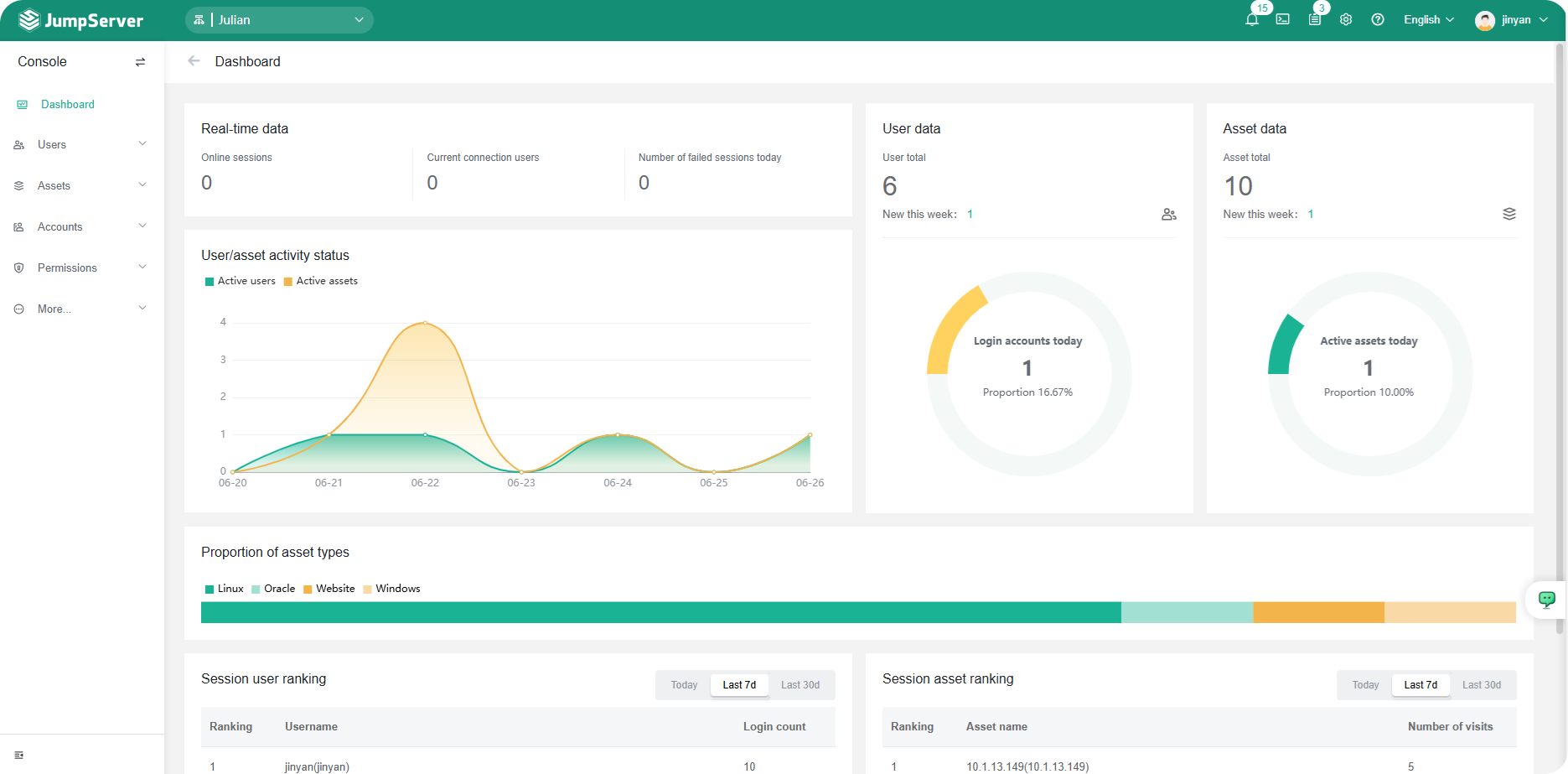
3 Page display⚓︎
4 Function list⚓︎
5 Application store⚓︎
JumpServer Remote Application feature supports Chrome, DBeaver by default in Community Edition,The Enterprise Edition offers more support for remote application, For more introduce of remote application you can click on the link for support.Application store。
6 Security statement⚓︎
JumpServer is a secure product. Please refer to the Basic Security Recommendations for deployment and installation。
If you discover any security issues, you can contact us directly:
- ibuler@fit2cloud.com
- support@fit2cloud.com
- 400-052-0755